Greetings!
If you were at Shmoocon this past weekend, you might remember a talk on Friday, done by Justin Morehouse and Tony Flick, on VMWare Guest Stealing. If you don’t, you probably started drinking too early. :) Anyway, somebody in the audience asked if there was a Nessus or Nmap script to detect this vulnerability. If I was the kind to yell things out, I would have yelled “there will be!” – and now, there is. It’ll be included in the next full version of Nmap, but in the meantime here’s how you can do it yourself.
Requires: Nmap 5.10BETA1 or higher (download directory)
Script: /blogdata/http-vmware-path-vuln.nse
Instructions: http://www.skullsecurity.org/blog/?p=459
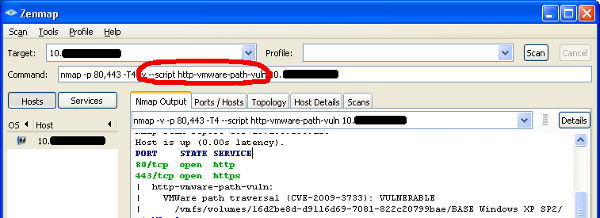
Details
This is a vulnerability in the VMWare management interface, which is a Web server. All you have to do is add a bunch of “../” sequences to the URL, and give it your chosen path, and it’ll let you grab any file on the filesystem. I’m not kidding, but I wish I was. You can even do the classic: https://x.x.x.x/sdk/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/etc/passwd
The applicable vulnerability identifiers are: CVE-2009-3733, VMSA-2009-0015.
The Nmap script simply downloads, parses, and displays the virtual machine inventory (assuming you’re in verbose mode – without verbose, it only prints ‘VULNERABLE’). The exploit released at Shmoocon will download the full vmware disk (vmdk) file, or you can do it yourself with your browser or wget.
Mitigation
DO NOT let anybody have access to the VMWare management interface (the web server). It should be on a separate network. That makes this attack significantly more difficult to perform.
Other than that, install the patches from the advisory.
UPDATE: I forgot to mention the punchline: ESX/ESXi run the Web server as root. /etc/shadow is fair game!

Comments
Join the conversation on this Mastodon post (replies will appear below)!
Loading comments...